HITRUST CSF
Control Threat Analysis
Cyber Threat Adaptive Quarterly Update
HITRUST uses a comprehensive and continuous process to identify threats, align mitigations that counter ongoing and new threats, and position the organization to respond effectively. The HITRUST CSF is regularly reviewed and updated as necessary to respond to the constantly shifting threat landscape through this process.

Static security programs can't keep up.
Cyber Threat Adaptive programs can.
Cyber threats evolve rapidly, static or slow-moving security frameworks and programs built around higher-level security objectives struggle to remain effective. Attackers move faster than ever, exploiting gaps and weaknesses before organizations can react. The result? Security controls that look good on paper but fail to respond a changing threat landscape.
At HITRUST, we’ve tackled this challenge head-on with our Cyber Threat Adaptive (CTA) program. This innovative solution stress-tests the HITRUST framework with real-world threat intelligence, ensuring our controls remain highly relevant and effective against emerging risks and support the organization’s ongoing compliance obligations.
Our report details findings covering the period from 09/01/2024 to 12/31/2024. Our research confirms that our i1, e1, and r2 requirement selections are responsive to the current threat landscape. During this period, we analyzed approximately 129,000 indicators across nearly 4,000 threat articles resulting in approximately 42,000 mappings to MITRE ATT&CK techniques and mitigations. Looking at the most common techniques identified, the e1 and i1 requirement selections have a high degree of coverage against techniques that were most prevalent in this quarter.
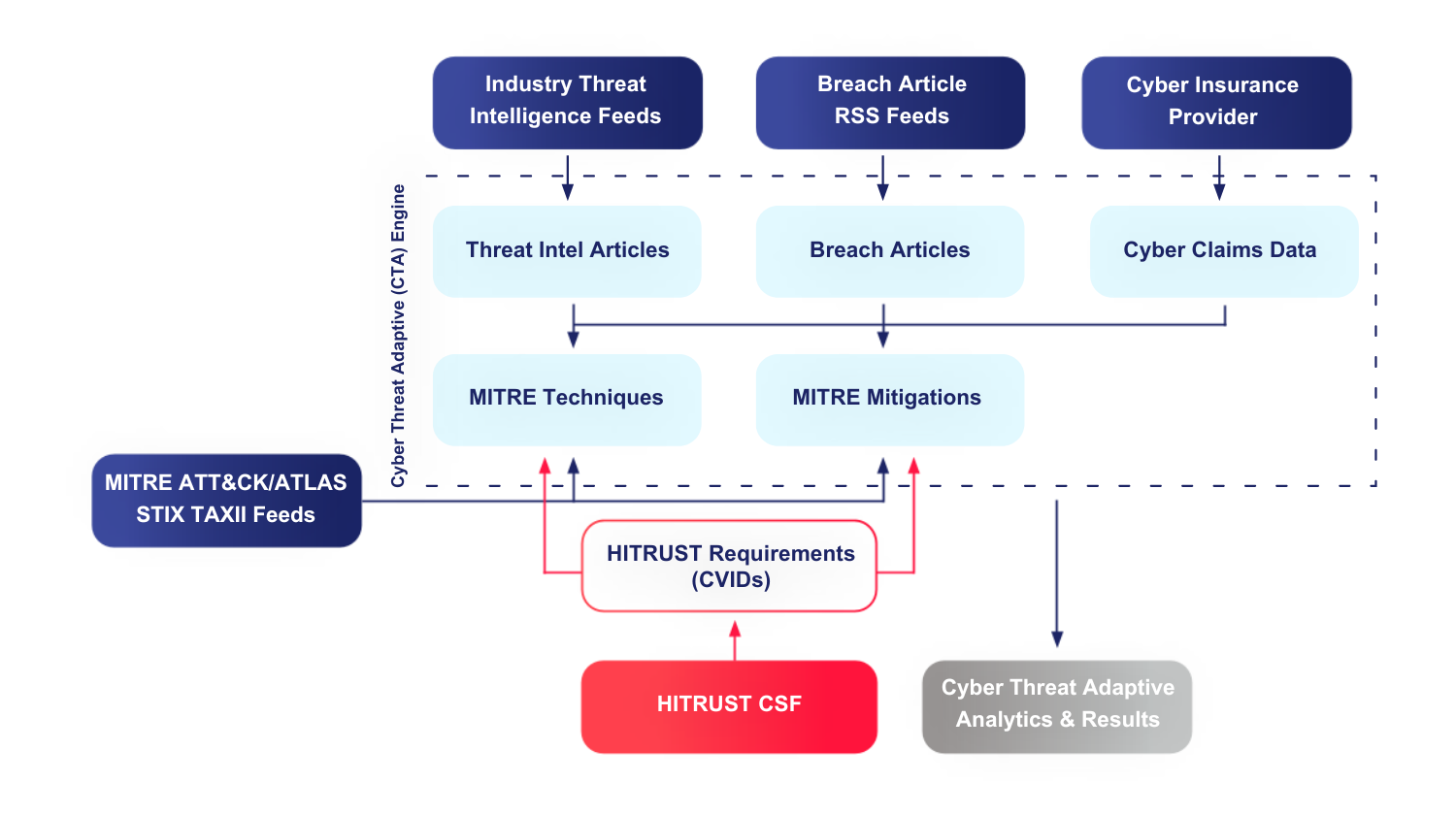
How it Works
Read the Latest Analysis
Our latest HITRUST CSF Control Threat Analysis covers the period from 09/01/2024 to 12/31/2024.
Check back here quarterly for updates.